Start Date & Duration
Saturday, 20th July 2024
30 hours
of live training with a
CEH Master Trainer
Sessions
Saturdays
10:00 AM to 6:00 PM
20th & 27th July 2024
3rd & 10th August 2024
Program Fee
INR 46,610
includes
1 Exam Voucher
Access to
EC Council iLabs and Course Materials for 6 Months + Access to RACE LMS for curated Course Materials
Other Benefits
Video Recordings of the sessions | Practice Quizzes | CEH Test Center at the Campus
Build your career with the most in-demand
cybersecurity certification in the world:
THE
CERTIFIED
ETHICAL
HACKER
The World’s No. 1 Ethical Hacking
Certification for 20 Years
Who is a Certified Ethical Hacker?
A Certified Ethical Hacker is a specialist typically working in a red team environment, focused on attacking computer systems and gaining access to networks, applications, databases, and other critical data on secured systems. A C|EH® understands attack strategies, the use of creative attack vectors, and mimics the skills and creativity of malicious hackers. Unlike malicious hackers and actors, Certified Ethical Hackers operate with permission from the system owners and take all precautions to ensure the outcomes remain confidential. Bug bounty researchers are expert ethical hackers who use their attack skills to uncover vulnerabilities in the systems.

Build your career with
the most in-demand
cybersecurity certification
in the world:
THE CERTIFIED
ETHICAL
HACKER
The World’s No. 1
Ethical Hacking
Certification for 20 Years
Who is a Certified Ethical Hacker?
A Certified Ethical Hacker is a specialist typically working in a red team environment, focused on attacking computer systems and gaining access to networks, applications, databases, and other critical data on secured systems. A C|EH® understands attack strategies, the use of creative attack vectors, and mimics the skills and creativity of malicious hackers. Unlike malicious hackers and actors, Certified Ethical Hackers operate with permission from the system owners and take all precautions to ensure the outcomes remain confidential. Bug bounty researchers are expert ethical hackers who use their attack skills to uncover vulnerabilities in the systems.

Ranked #1
Certifications by ZDNet
Ranked as a Top 10
Certification
C|EH® Ranks 4th
Cybersecurity Certifications
Ranked #1
Certifications by ZDNet
Ranked as a Top 10
Certification
C|EH® Ranks 4th
Cybersecurity Certifications
What is C|EH® v12?
The Certified Ethical Hacker has been battle-hardened over the last 20 years, creating hundreds of thousands of Certified Ethical Hackers employed by top companies, militaries, and governments worldwide.
In its 12th version, the Certified Ethical Hacker provides comprehensive training, handson learning labs, practice cyber ranges for engagement, certification assessments, cyber competitions, and opportunities for continuous learning into one comprehensive program curated through our new learning framework: 1. Learn 2. Certify 3. Engage 4. Compete.
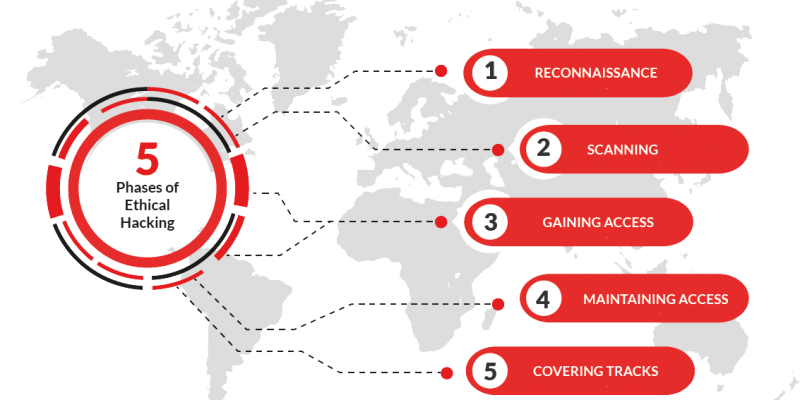
The C|EH v12 also equips aspiring cybersecurity professionals with the tactics, techniques, and procedures (TTPs) to build ethical hackers who can uncover weaknesses in nearly any type of target system before cybercriminals do.
What’s New in the C|EH® v12
LEARN | CERTIFY | ENGAGE | COMPETE
The C|EH® v12 is a specialized and one-of-a-kind training program to teach you everything you need to know about ethical hacking with hands-on training, labs, assessment, a mock engagement (practice), and global hacking competition. Stay on top of the game with the most in-demand skills required to succeed in the field of cybersecurity.
Master ethical hacking skills
that go beyond the certification.
Course Outline
20 Modules That Help You Master the Foundations of Ethical Hacking and Prepare to Take the C|EH Certification Exam
Cover the fundamentals of key issues in the information security world, including the basics of ethical hacking, information security controls, relevant laws, and standard procedures.
Learn how to use the latest techniques and tools to perform foot printing and reconnaissance, a critical pre-attack phase of the ethical hacking process.
Learn different network scanning techniques and countermeasures.
Learn various enumeration techniques, such as Border Gateway Protocol (BGP) and Network File Sharing (NFS) exploits, and associated countermeasures.
Learn how to identify security loopholes in a target organization’s network, communication infrastructure, and end systems. Different types of vulnerability assessment and vulnerability assessment tools.
Learn about the various system hacking methodologies—including steganography, steganalysis attacks, and covering tracks—used to discover system and network vulnerabilities.
Learn different types of malware (Trojan, virus, worms, etc.), APT and fileless malware, malware analysis procedure, and malware counter measures.
Learn about packet-sniffing techniques and how to use them to discover network vulnerabilities, as well as countermeasures to defend against sniffing attacks.
Learn social engineering concepts and techniques, including how to identify theft attempts, audit human-level vulnerabilities, and suggest social engineering countermeasures.
Learn about different Denial of Service (DoS) and Distributed DoS (DDoS) attack techniques, as well as the tools used to audit a target and devise DoS and DDoS countermeasures and protections.
Understand the various session hijacking techniques used to discover network-level session management, authentication, authorization, and cryptographic weaknesses and associated countermeasures.
Get introduced to firewall, intrusion detection system (IDS), and honeypot evasion techniques; the tools used to audit a network perimeter for weaknesses; and countermeasures.
Learn about web server attacks, including a comprehensive attack methodology used to audit vulnerabilities in web server infrastructures and countermeasures.
Learn about web application attacks, including a comprehensive web application hacking methodology used to audit vulnerabilities in web applications and countermeasures.
Learn about SQL injection attacks, evasion techniques, and SQL injection countermeasures.
Understand different types of wireless technologies, including encryption, threats, hacking methodologies, hacking tools, Wi-Fi sedcurity tools, and countermeasures.
Learn Mobile platform attack vector, android and iOS hacking, mobile device management, mobile security guidelines, and security tools.
Learn different types of IoT and OT attacks, hacking methodology, hacking tools, and countermeasures.
Learn different cloud computing concepts, such as container technologies and server less computing, various cloud computing threats, attacks, hacking methodology, and cloud security techniques and tools.
Learn about encryption algorithms, cryptography tools, Public Key Infrastructure (PKI), email encryption, disk encryption, cryptography attacks, and cryptanalysis tools.
Prove Your Skills and Abilities With Online, Practical Examinations
The Certified Ethical Hacker® credential is trusted globally as the industry standard for evaluating one’s understanding of ethical hacking and security testing. As an ANSI 17024 accredited examination, the 150-question, 4-hour proctored exam is recognized across the globe as the original and most trusted tactical cyber security certification for ethical hackers. Certification domains are carefully vetted through industry practitioners, ensuring the certification maps to current industry requirements; this exam undergoes regular psychometric evaluation and tuning to ensure a fair and accurate measure of the candidate’s knowledge in the ethical hacking domain.



