Harnessing CNAPP: A Guide to Understanding and Implementing Cloud Security

As organizations increasingly transition to cloud-native architectures, ensuring robust security across these dynamic environments is becoming more critical than ever. The Cloud Native Application Protection Platform (CNAPP) offers a comprehensive solution by integrating security, compliance, and threat detection into cloud-native infrastructures. CNAPP enables continuous protection throughout the application lifecycle, from development to deployment, ensuring businesses can effectively secure their cloud applications against emerging threats.
In recognition of the importance of this technology, REVA Academy for Corporate Excellence (RACE) recently conducted a specialized workshop on CNAPP, facilitated by Prof. Papa Rao. The workshop provided an in-depth exploration of cloud-native security and equipped participants with practical strategies to safeguard their cloud environments efficiently.
The Importance of Cloud-Native Architectures
The workshop kicked off with a deep dive into cloud-native architectures. Prof. Rao explained that cloud-native applications are designed to leverage the elasticity and distributed nature of the cloud. This approach contrasts traditional on-premises infrastructures, enabling organizations to scale components independently and deploy updates without downtime.
Cloud Security Challenges and CNAPP Solutions
Moving on to security, Prof. Rao highlighted the complexities that arise from managing security in a cloud-native environment. With applications split into microservices, traditional security tools fall short. Here’s where CNAPP comes into play.
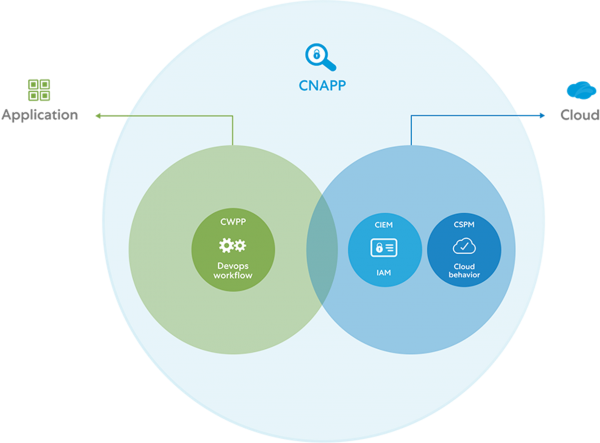
What is a Cloud Native Application Protection Platform (CNAPP)?
Defined by Gartner, CNAPP consolidates various security tools into one unified platform. It offers an end-to-end solution that spans from development to runtime, significantly simplifying cloud security management.
Real-World CNAPP Use Cases
To illustrate CNAPP’s effectiveness, Prof. Rao discussed several real-world use cases:
- Preventing Compliance Violations: CNAPP helps organizations remain compliant with various security standards, such as NIST and PCI DSS.
- Securing Multi-Cloud Environments: CNAPP supports multiple cloud platforms, making it invaluable for businesses operating in hybrid cloud environments.
- Container Security: As containers become more prevalent in cloud-native deployments, CNAPP provides real-time scanning and threat detection, ensuring they remain secure throughout their lifecycle.
Exploring Top CNAPP Platforms
Prof. Rao also provided an overview of leading CNAPP platforms, including:
Microsoft Defender for Cloud
CrowdStrike Falcon Cloud Security
Runecast
CloudGuard CNAPP
Each platform offers unique capabilities, from visibility into security postures to advanced threat protection and multi-cloud governance.
The Shift Towards Cloud Agnostic
As cloud-native applications become more prevalent, organizations face the challenge of multi-cloud environments. Different cloud providers (like Azure, AWS, and GCP) have unique APIs, security implementations, and service offerings, prompting the rise of the cloud-agnostic approach.
Cloud-Native vs. Cloud Agnostic
Cloud-Native
Applications built specifically for a particular cloud provider, optimized to leverage that provider’s capabilities.
Cloud Agnostic
Applications designed to be portable across multiple cloud platforms, allowing organizations flexibility in choosing the best services and pricing from various providers.
Azure Policies: The Foundation of Security Governance
Azure Policies serve as a core governance feature designed to ensure compliance and streamline security in cloud environments. It is a critical tool for enforcing security best practices, and one of the standout features available only in Azure when compared to AWS. By using Azure Policies, organizations can define rules and automatically enforce those rules across Azure resources.
Key Features of Azure Policies:
- Security and Governance: Azure Policies enforce both governance and security across all Azure resources. From enforcing specific resource types to ensuring tagging and configuration consistency, these policies make it easy to manage security across an enterprise.
- JSON-based Policies: Azure Policies are written in JSON format, making it straightforward to customize governance for specific business needs.
- Predefined Security Initiatives: Microsoft provides built-in policy initiatives such as the CIS benchmark and Azure Foundation benchmark. These initiatives simplify governance by bundling multiple policy definitions aimed at achieving specific security objectives.
Security Initiatives and Compliance
A security initiative is a collection of policy definitions bundled together to achieve a specific goal, such as adhering to the CIS (Center for Internet Security) benchmark or other compliance frameworks. By using initiatives, you can apply a set of security policies consistently across all resources, ensuring they meet regulatory requirements.
Key Initiatives Include:
- Azure Foundation Benchmark: This initiative includes policies for foundational security controls, covering critical areas like identity management, logging, and threat protection.
- CIS Benchmark: This initiative aligns with the CIS guidelines, ensuring resources in Azure adhere to security best practices.
Microsoft Defender for Cloud: Multi-Cloud Security Simplified
Microsoft Defender for Cloud integrates Cloud Security Posture Management (CSPM) and Cloud Workload Protection Platform (CWPP) into a single solution. It allows users to manage security not only in Azure but also across AWS and GCP. This unified approach gives organizations real-time visibility into their security posture and actionable recommendations to mitigate risks.
Unified Platform for Multi-Cloud Environments
One of the most powerful features of Defender for Cloud is its ability to manage multi-cloud environments. By integrating AWS and GCP, organizations can monitor their resources and security compliance from a single pane of glass.
For example, after integrating AWS with Defender for Cloud, you can view security recommendations, monitor vulnerabilities, and improve your security score in real-time across all environments. Azure automates this integration through connectors that are easy to set up. For AWS, users can quickly configure access by running CloudFormation or Terraform scripts to create roles, allowing Defender for Cloud to scan AWS resources.
Steps to Integrate AWS:
- Set up an AWS account in Defender for Cloud.
- Use predefined CloudFormation or Terraform templates to configure access roles in AWS.
- View and manage security posture in Defender for Cloud alongside Azure resources.
Conclusion
Managing security and compliance in a multi-cloud world can be challenging. Azure Policies simplify governance across cloud environments, while Microsoft Defender for Cloud offers a unified security view. With features like automated remediation and CIS benchmark initiatives, Azure leads in multi-cloud security.
The workshop also showcased the Cloud Native Application Protection Platform (CNAPP) as a transformative force in DevSecOps. By seamlessly integrating security tools, CNAPP not only bolsters cloud-native security but also champions early “shift-left” practices, ensuring that security is woven into the development process from the very start.
Check out here to learn more about our bespoke program on MSc in Cloud Architecture and Security to learn more about managing multi cloud platforms and security controls. This program is suitable for working professionals with a minimum of 3-4 year experience in IT.
Visit our website race.reva.edu.in or Call: +91 80693 78092 or write to us: enquiry@race.reva.edu.in.
We look forward to seeing you at our next event!



